Table of Contents
Mobile Phone Honeypot
Introduction
“a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems.” - Wikipedia.org
In March 2021, I started developing a device to answer incoming calls and pretend to be a human answering the call. The purpose of this device is to log information and evidence regarding people calling without permission (generally telemarketers, scams, and phishing attempts). The idea is inspired by computer honeypots which are designed to be connected to by malicious users in order to collect evidence and monitor what they are doing.
The Hardware
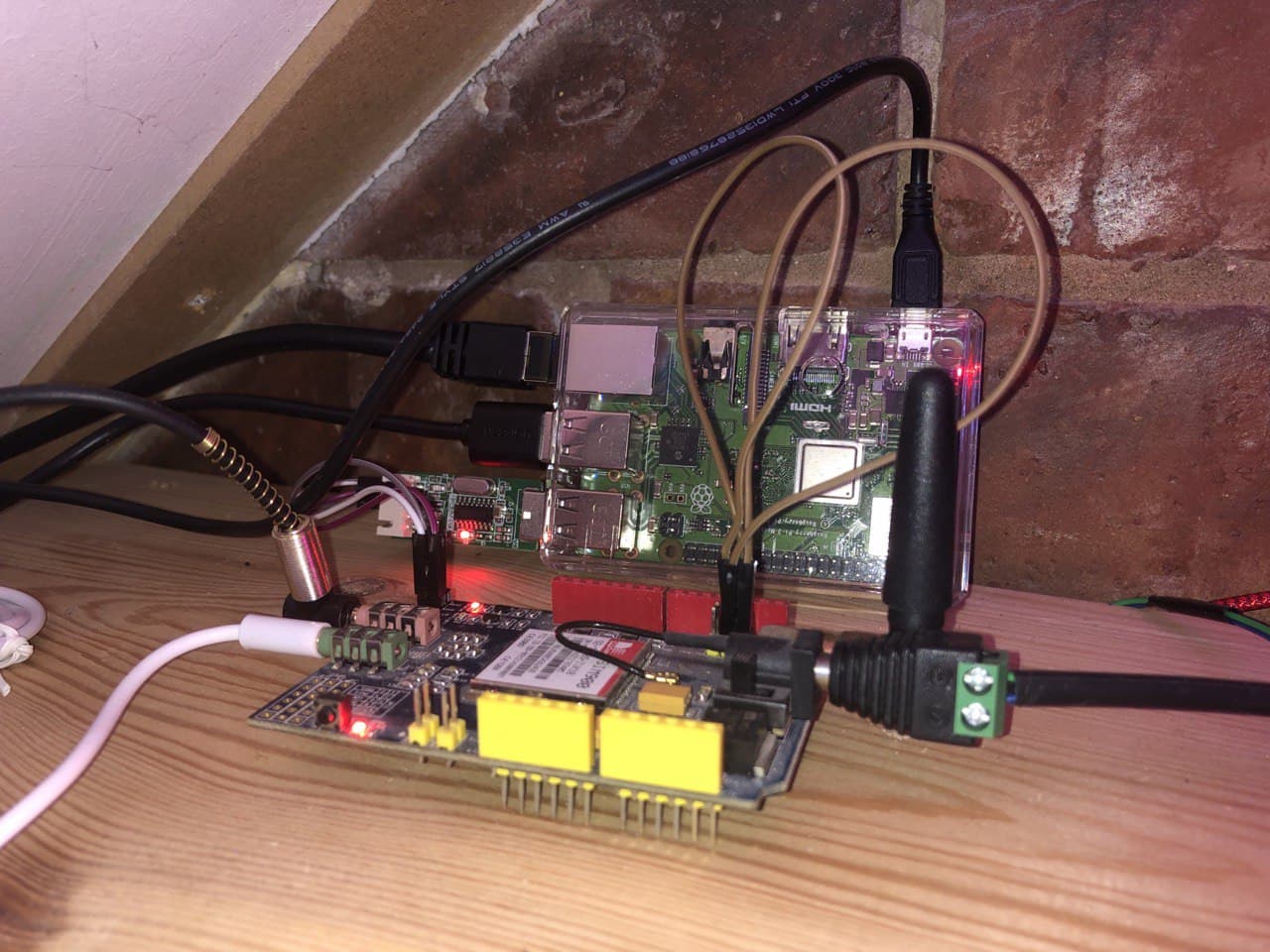
I am using the following hardware:
- A Raspberry Pi 3
- A SIM900L Arduino Uno GSM Shield
- A USB sound card (with microphone and speaker jacks)
- A USB to serial adapter
I have connected the GSM shield directly to a USB serial adapter plugged into the Raspberry Pi. Technically a USB adapter isn't needed at all because the Pi has GPIO serial but the adapter handles voltage differences for me and reduces the chance of killing the Raspberry Pi with bad connections.
The shield's microphone in is connected to the speaker out on the Pi. The shield's speaker out is connected to the microphone in on the Pi.
The Software
I have a Python script running continuously on the Pi which acts as a serial proxy with Node-Red. This allows me to use Node-Red for the majority of the scripting. When a call comes in, the shield sends a message over serial to the Pi. Whenever this message is detected, the Pi runs 2 additional scripts: speak, and record. This message is forwarded to Node-Red (along with all other messages) for further logic to be executed.
The record script immediately starts recording audio from the mic in and also the speaker out; this allows both sides of the conversation to be recorded. This audio is saved directly onto my home server so the Pi's SD card doesn't keep getting written to.
The speak script waits 5 seconds and then starts playing audio samples which contain pre-recorded human speech. I was originally using text-to-speech but it wasn't human enough to be convincing. I have various phrases recorded in different audio files so I can edit what is said quite easily.
Node-Red immediately starts executing a “flow” when the “incoming call” message is received. It parses the phone number the caller is using, saves it to a database, then sends me a message via a Telegram bot so I know there is an incoming call. After a few seconds of delay, it replies to the Pi to instruct the shield to answer the call.
Once the call is answered, all relevant software has already been running for multiple seconds and everything is ready to go. The caller will hear someone “responding” to what they are saying. For now, everything is pre-recorded and there is no logic to change the speech in any way during the call. In the future, I would like to add silence detection so that my speech is only played when the caller stops speaking. A few callers have noticed a robot was “responding” to them because it kept talking over them.
Attracting Some Callers
I bought a SIM card to be dedicated to this project which means the phone number I am using is only a week old. I needed to get the number “out there” so people would start calling. I signed up to multiple suspicious websites and used a unique fake name on each one of them. So far, I have discovered where most of the telemarketers got my phone number from because they started the call with “Hi, can I speak to (fake name)?”
I posted the phone number inside an invisible div on some of my websites for a few hours. This was discovered by the Google web crawler and I assume some other crawlers too. I expect this will help the malicious automated calls find the number quicker.
Observations
I have been running this project for less than a week. So far, I have noticed that some telemarketers are incredibly persistent and sometimes call up to 6 times per day. I have also noticed they seem to respect “quiet hours” and don't call in the middle of the night despite calling from other countries. I also don't seem to get calls on Saturdays or Sundays.
I have not yet received any phishing attempts or obvious scam calls (but I have received scam SMS messages). The majority of calls have started as a result of me entering the phone number in one of those “You've won a free prize!!1” websites; this alone caused 15 calls on Monday.
Car insurance comparison sites have (so far) respected my preferences to not be contacted. I even told them I had a car accident in the last month and this hasn't caused any phone calls at all yet.
I had a call which lasted for over an hour (it only ended because I manually disconnected). The caller was silent for the entire time but called back the next day attempting to sell me some kind of funeral plan. This makes me assume they have autodialling software which screwed up.
The Data
Right now, all the collected data is saved but has no interface to view it easily. I intend to make a public page with the call log (but not the recordings) eventually. So far, every number which called has already been reported multiple times on other websites.
Hopefully a public page will give some credibility to people reporting pushy telemarketers. For example, a caller claiming to be acting on behalf of the Three UK mobile network has called 16 times this week. I can't say for sure if they're genuinely related to Three but a page with the logs might encourage companies such as Three to review their telemarketing strategy.