Table of Contents
Hacky Holidays Challenge
Introduction
The Hacky Holidays cybersecurity CTF ran between the 11th December 2020 to the 3rd of January 2021 and could be accessed via hackazon.org. I took part and finished in 35th place.
I forgot to note down some of the challenge names; for that reason, I may not include a name for every challenge. Also, some challenges I didn't even write notes for so this isn't a full list.
Challenge One
Not the first challenge, just the first challenge I forgot to include the name of.
Challenge description: “Tell Santa your name and he might give you a flag for Christmas!”
For this challenge we were given the above clue and some C code which included the following:
typedef struct locals {
char username[50];
char role[10];
} locals;
Raw user input was assigned to this struct, so I could see that by entering 50 bytes the value of role could be influenced. Further in the code, role is compared with a static string “admin” to decide if the flag should be returned or not. Entering “jjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjjadmin” is enough to make this if statement return true.
Challenge Two
Not the second challenge, just the second challenge I forgot to include the name of.
Challenge description: “Such beautiful christmas scenery! .. But maybe it's concealing a secret message?”
This stego challenge consisted of an average-looking Christmas image which had a hidden flag written at the bottom. I used https://incoherency.co.uk/image-steganography/ to reveal the text at the bottom, but I had to adjust the colours of the output image to make it easier for me to read. I did this quite quickly but kept getting the wrong flag because I forgot to wrap the answer in CTF{}
This is part of the image which shows the flag (after editing to make the text visible).
Challenge Three
Not the third challenge, just the third challenge I forgot to include the name of.
Challenge description: “I wrote a quick CV to apply as a programmer for Santa. Can you quickly review it before I submit it?”
I didn't complete this challenge, but I got very close
This challenge requires you to provide a name, and then a PDF (a CV) will be generated for you and returned. The “name” is added straight into the PDF and it's generated with LaTeX so various injection vulnerabilities are present. It is possible to send “\input{filename}” as the “name” variable and get that file returned in the PDF.
I tried various things here and I'm also about 95% sure I crashed the Docker container this challenge was running in on the Hackazon servers (sorry). Unfortunately, nothing I tried actually gave me a flag but I do feel like I was very close.
Challenge Four
Not the fourth challenge, just the fourth challenge I forgot to include the name of.
Challenge description: “Did you lose any gifts and need to find it again? We offer customer support!”
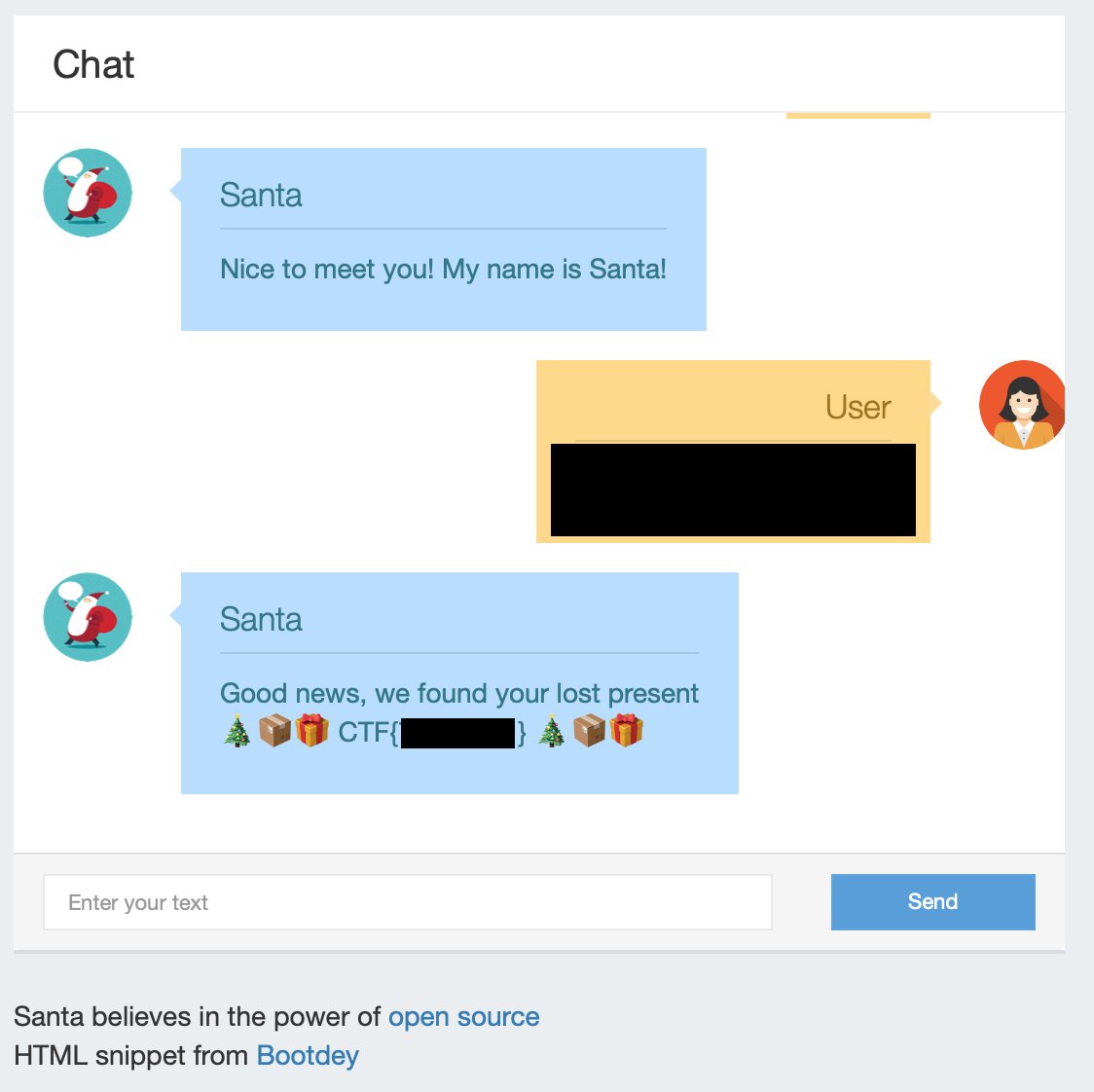
This challenge consisted of a “customer support bot” for Santa as shown below:
The fake customer support bot asks for a voucher code which you are expected to send in this format “voucher 12345678”. Upon entering a voucher, a JSON object is constructed where “action” is “redeemVoucher” and “voucherCode” is your raw input. This JSON object is used to make an API request.
The voucher API request always returns a non-200 status code but by looking at the source code we can see that a 200 response code is required for the flag to be returned. In addition, the source code shows another API endpoint for checking the server health: this simply returns a 200 status code every time.
By sending voucher “,”action“:“health we can change “action” from “redeemVoucher” to “health” which causes the API to return 200 and the flag to be returned.
Challenge Five
Not the fifth challenge, just the fifth challenge I forgot to include the name of.
Challenge description: “Can you help Santa test the security of a web service?”
This challenge shows a webpage which allows you to view the HTTP response code of any URL you type in. There’s a hint under the form which says “ToDo: fix firewall issues to allow outbound access.” By typing in 127.0.0.1 we are able to get a ‘200’ response. By inspecting the POST request, I noticed a “statusOnly” variable which was set to ‘1’, by changing this to ‘0’ we are able to also get the HTTP body in our response. By requesting http://127.0.0.1/server-status I found a list of active requests which also showed a request to 127.0.0.1:8000 - This is where the flag was located.
Challenge Six
Not the sixth challenge, just the sixth challenge I forgot to include the name of.
Challenge description: “Does DNS hold any secrets for you?”
Part One
For this challenge, I was given the following clue: “We've hidden a flag in the DNS of flagplz.hhchallenge.com. Can you find out what we want for Christmas? You need the right record type!”
By running “dig TXT flagplz.hhchallenge.com” I saw “milkandcookies.hackyholidays.io” — The flag was “milkandcookies”
Part Two
The challenge is: “We forgot which subdomain we were hosting our flags on, can you find it? ?.hhchallenge.com.”
By searching for “hhchallenge.com” on censys.io, I found a certificate for a subdomain: “f8fc793de19232.hhchallenge.com”.. this was the flag.
Happy Buckets
Challenge description: “Aiming for digitalization, Santa Claus have set up a site for registering wishes on the Internet. How far can you go to ensure you get the gifts you want this Christmas?”
Part One
Challenge Title: HEAPS, BUNCHES, LOADS, MYRIADS, TONS
This challenge consists of a webpage which has a web form which allows you to submit a message. This page is hosted on AWS and the title of the challenge is “HAPPY BUCKETS”, which pointed me in the direction of the S3 bucket the site was using for assets. Sure enough, “happybucketscontent.s3.eu-west-2.amazonaws.com” was the source of the assets and that page had a directory listing publicly accessible which revealed a file called “284e16e1af4903d74cc88ce9f0cf8c92.txt” which contained the flag.
Part Two
Challenge Title: Reversing
I also found a file called “Santa-Letters-jar-with-dependencies.jar” on the unprotected S3 bucket which yielded many directories and files when extracted.
Since the title is “reversing”, the challenge author probably expected me to do something more technical than what I actually did. I simply did a recursive grep in the directory for “CTF{” and found the flag I needed. I don't think it was meant to be that easy.
Candle Locator
This challenge consisted of an image and the flag was the street name of where the photo was taken. The image had GPS metadata so I simply Googled the GPS coordinates and copied the street name.
Present Drop
This challenge consisted of a .pcap file. The flag text was written on a .png file which could be extracted from the packet capture file.
Hacky Travels
Part One
Challenge Title: HTML
The first flag was stored in the HTML as a meta object: <meta name=“ctfflag” content=“CTF{hacky_html_reading}”>
Part Two
Challenge Title: Disabled
The HTML also contains a disabled button which calls a Javascript function when clicked. I manually ran the function giveflag() using the Javascript console. The flag was then given to me in an alert dialog.
Reinder
Part One
Challenge Title: Santa's Profile
This challenge consists of a “dating site” for reindeer. The task was to find Santa’s profile. Each profile has a numerical ID so we can find Santa’s by checking each ID manually.
Part Two
Challenge Title: Packed
The source code for this challenge has a main.js file which references a .map file. The .map file contains the flag.
Part Three
Challenge Title: Robotic Backups
The challenge description tells us we are looking for a backup file (or files). I visited /robots.txt to see if any directories or files were disallowed by search engines and found “/DataBackup.zip”. This zip file contained a flag.txt file.
Part Four
Challenge Title: Admin
There is an “isAdmin” cookie which can be changed to “true” to reveal a flag.
Part Five
Challenge Title: Santa's Location
When you visit Santa's profile, a distance is shown. This distance represents how far away you currently are from Santa. You are able to change your own location easily simply by editing a cookie.
This challenge could have been solved with a script, but I did it manually which probably took less time than writing the script would have :)
Simply by changing my own coordinates and refreshing the page, I could watch as my location got closer (or further away). Eventually I got close enough that I could determine a street name which was used as the flag.
Part Six
Challenge Title: CVE
I was given this clue: “The website is using a vulnerable JavaScript library related to an injection into “HTML option elements” … can you tell us the CVE number? Flag format: CVE-xxxx-xxxxx”
The only library in use by this site is jQuery so this CVE was easily found by googling for vulnerabilities in jQuery 3.4.1. I found this page which listed two CVEs: https://www.cybersecurity-help.cz/vdb/SB2020042126